Dual ring topology is a network configuration that uses two concurrent rings of connections to link devices. This redundant network structure enhances reliability and provides a failover mechanism, ensuring high availability and network uptime. Unlike simpler topologies, dual ring offers an extra layer of protection against network failures.
Types of Dual Ring Topology
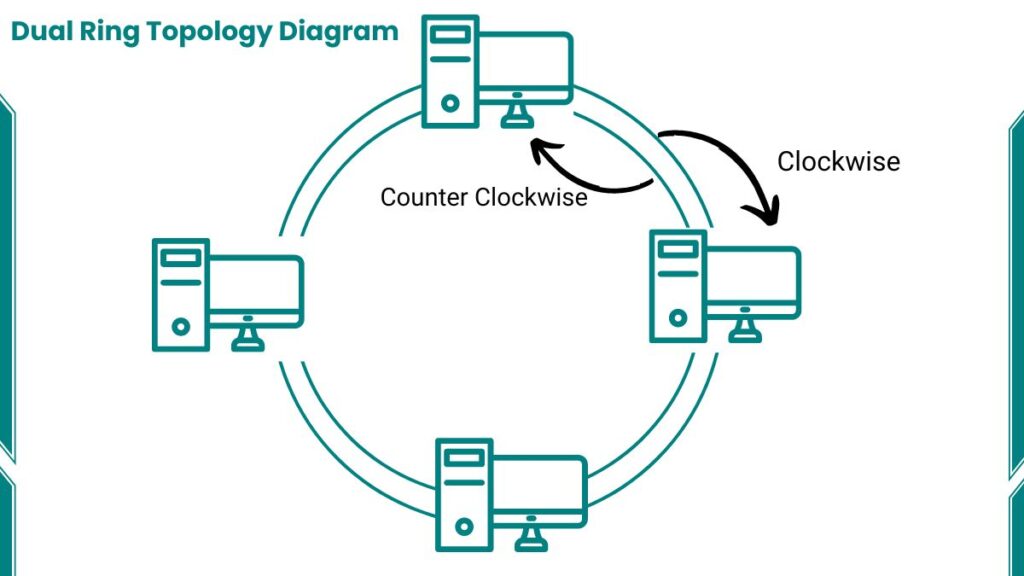
- Counter-Rotating Rings: In this type, data travels in opposite directions on each ring. They maximize efficiency and provide quick rerouting in case of failures.
- Parallel Rings: Both rings transmit data in the same direction. It offers redundancy but potentially slower recovery times compared to counter-rotating rings.
Dual Ring Topology Example
Imagine a corporate office with multiple departments. Each department has a computer connected to both rings. If one ring fails, data can still flow through the other, maintaining communication across the organization. This setup demonstrates the network resilience inherent in dual-ring configurations.
Dual Ring Architecture
The architecture of a dual-ring topology consists of:
- Nodes: Devices (computers, servers, switches) connected to both rings.
- Rings: Two separate paths for data transmission.
- Connectors: Hardware that links nodes to the rings.
- Network Interface Cards (NICs): Special cards that allow devices to connect to both rings simultaneously.
This architecture ensures that each node has two potential paths for sending and receiving data, significantly improving network reliability.
Dual Ring Protocol
The most well-known protocol for dual ring topologies is the Fiber Distributed Data Interface (FDDI). FDDI uses a token-passing mechanism to control data flow and manage network traffic efficiently. When a failure occurs, FDDI can quickly reconfigure the network, rerouting data through the functional ring to maintain connectivity.
Advantages of Dual Ring Topology
- High Reliability: The redundant nature of dual rings significantly reduces the risk of network downtime.
- Improved Performance: With two rings, network traffic can be balanced, leading to better overall performance.
- Fault Tolerance: If one ring fails, the other can take over, ensuring continuous operation.
- Scalability: Dual ring networks can be easily expanded to accommodate growth.
- Enhanced Security: The closed-loop structure makes it harder for unauthorized access.
Disadvantages of Dual Ring Topology
- Cost: Implementing a dual-ring topology is more expensive than simpler configurations due to additional hardware requirements.
- Complexity: Setting up and maintaining a dual-ring network can be more challenging, requiring specialized knowledge.
- Potential for Double Failures: Although rare, if both rings fail simultaneously, the entire network can go down.
- Limited Flexibility: Once set up, changing the network structure can be difficult and costly.
Use Cases of Dual Ring Topology
- Financial Institutions: Banks and stock exchanges rely on dual ring topologies for uninterrupted transactions and data security.
- Healthcare Systems: Hospitals use dual-ring networks to ensure constant access to critical patient information.
- Telecommunications: Service providers implement dual-ring topologies to maintain reliable communication services.
- Industrial Control Systems: Factories and power plants use dual-ring networks for continuous monitoring and control of critical processes.
- Transportation Networks: Air traffic control systems and railway networks benefit from the high reliability of dual-ring topologies.
Comparison with Other Topologies
When compared to a star topology, the dual ring offers better fault tolerance but at a higher cost. Mesh topology provides similar reliability but can be more complex and expensive to implement for large networks. The choice between these depends on specific needs, budget constraints, and desired network characteristics.

