Computers and networks face many online threats today. Hackers, viruses, and cyber-attacks are common. That’s why protecting your network is very important. One of the most powerful tools for this purpose is a hardware firewall.
Hardware Firewall Definition
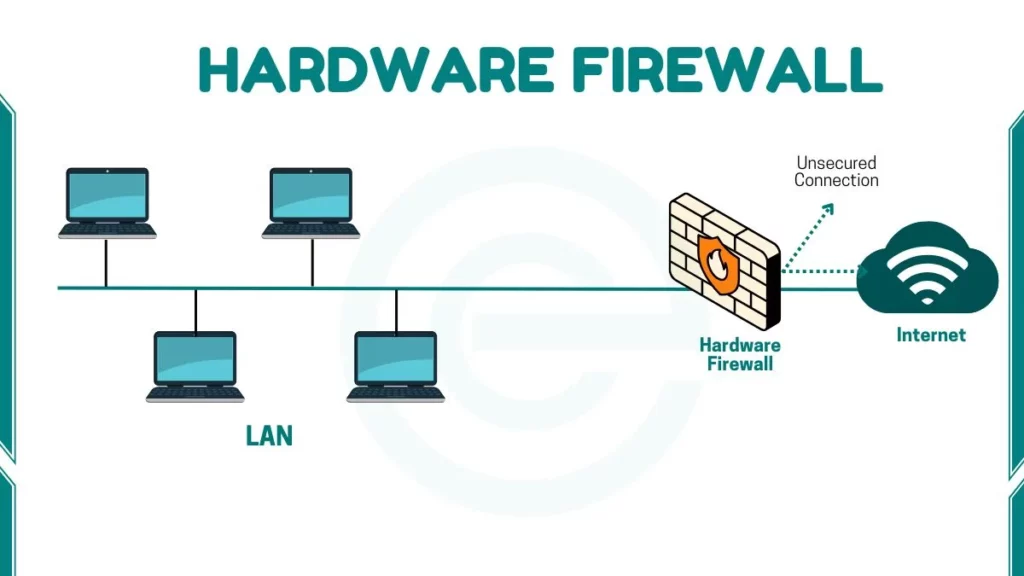
A hardware firewall is defined as a physical security device that protects a computer network from unauthorized access. It filters the data that comes in and goes out of a network. In simple words, it works as a barrier between your internal network and the internet.
It stops hackers, viruses, and malicious traffic before they reach your computers. Unlike software firewalls that run inside your system, a hardware firewall works independently as a dedicated device.
Hardware Firewall Meaning
The meaning of a hardware firewall is that the word hardware shows that it is a tangible device, not a program. The word firewall means a barrier that stops fire from spreading. Similarly, in computing, it stops harmful data or attackers from entering your network.
You can think of it like a security guard standing between your home (your internal network) and the street (the internet). It checks every visitor and allows only safe ones to enter.
Hardware Firewall Types
There are different types of hardware firewalls. Each works in its own way and serves different needs:
1. Packet-Filtering Firewall
A Packet-Filtering Firewall is the most basic and oldest type of firewall. It works by checking small units of data called packets that travel across the network.
Each packet contains information like the source IP address, destination IP address, port number, and protocol. The firewall looks at these details and decides whether to allow or block the packet based on predefined security rules.
2. Stateful Inspection Firewall
A Stateful Inspection Firewall (also known as a Dynamic Packet-Filtering Firewall) is more advanced than basic packet filtering.
It not only checks the packet headers but also keeps track of active connections and the state of network sessions. This means it remembers previous packets and understands the context of communication.
3. Proxy Firewall
A Proxy Firewall acts as a middleman between the user and the internet. Instead of allowing direct communication between devices and web servers, it processes all requests through itself first.
When you send a request to visit a website, the proxy firewall receives it, checks it for safety, and then forwards it to the internet. The response from the website also goes through the firewall before reaching your computer.
4. Next-Generation Firewall (NGFW)
A Next-Generation Firewall (NGFW) is the modern and most powerful type of firewall. It includes all the functions of traditional firewalls but adds advanced security technologies to fight today’s cyber threats.
NGFWs can perform Deep Packet Inspection (DPI). Which means they check the contents of data packets not just headers. They can also detect and block malware, spyware, and ransomware attacks in real time.
5. Unified Threat Management (UTM) Firewall
A Unified Threat Management (UTM) firewall combines multiple security features into a single hardware device. It provides a complete solution for small and medium-sized organizations that want strong protection without managing several separate tools.
A UTM typically includes:
- Firewall and VPN functions
- Intrusion Detection and Prevention (IDS/IPS)
- Anti-virus and anti-spam filtering
- Web and content filtering
- Network monitoring and reporting tools
Choosing the right type depends on your network size, budget, and security level.
Hardware Firewall Architecture
The architecture of a hardware firewall includes both hardware components and software control systems.
- Hardware components include processors, memory, ports, and network interfaces.
- Software systems manage the rules, filtering, and logging.
A typical firewall uses a firmware-based operating system that controls how data moves through it. The internal architecture uses routing engines, inspection engines, and logging modules to ensure safe communication.
This design helps it handle large amounts of data quickly without slowing down the network.
How the Architecture Works Together
Here’s how everything works in a simple flow:
- Incoming data from the internet enters the firewall through a network port.
- The filtering engine checks the packet’s IP address and port number.
- The inspection engine looks deeper into the content to find any harmful code.
- If the data is safe, the routing engine sends it to your network.
- If it is dangerous, the logging module records it, and the packet is blocked.
This process happens in just a few milliseconds, keeping your connection fast and secure.
Hardware Firewall Features
Modern hardware firewalls offer many smart features that make them powerful security tools.
Some common features include:
- Stateful Inspection: It tracks the state of active connections and allows only safe ones.
- VPN Support: It lets users securely connect to private networks remotely.
- Intrusion Detection and Prevention (IDS/IPS): It identifies and blocks suspicious behavior in real time.
- Content Filtering: It blocks harmful websites or unwanted content.
- Logging and Reporting: It records all network activities for monitoring.
- Cloud Integration: Many new devices connect with cloud services for better updates and threat intelligence.
These features make hardware firewalls strong defenders for both small and large networks.
Hardware Firewall Example
Here are some popular examples of hardware firewalls used in real-world networks:
- Cisco ASA (Adaptive Security Appliance): common in enterprise environments.
- Fortinet FortiGate: It is known for performance and reliability.
- Sophos XG Firewall: It offers user-friendly management and reporting.
- Palo Alto Networks Firewall: It is famous for advanced threat detection.
- WatchGuard Firewall: It is suitable for small and medium businesses.
These examples show how different organizations use hardware firewalls for protection and control.
Hardware vs Software Firewall
| Feature | Hardware Firewall | Software Firewall |
|---|---|---|
| Type | Physical device | Program installed on a computer |
| Protection Scope | Entire network | Single device |
| Speed | Faster | Depends on system performance |
| Maintenance | Requires setup | Easy to install |
| Ideal For | Businesses and offices | Personal computers |
For more depth detail information read Difference Between Hardware Firewall and Software Firewall.
Hardware Firewall Equipment
To set up a hardware firewall, you need certain equipment. These include:
- Firewall appliance (the main device)
- Network cables to connect to routers and switches
- Power supply
- Router or modem connected to the internet
- Computer or console to configure settings
In larger setups, IT teams use rack-mounted firewalls inside data centers. Home users often use small firewall routers for basic security.
Hardware Firewall Setup Guide
Setting up a hardware firewall is simple if you follow these basic steps:
- Connect the firewall between your modem and router.
- Turn it on and connect your computer to it using a LAN cable.
- Access the admin panel (usually through a web browser).
- Set up basic security rules – allow safe traffic, block unwanted access.
- Enable features like intrusion prevention and content filtering.
- Update firmware to keep protection current.
FAQs
How is a hardware firewall managed?
It is managed through a web interface or management console. Administrators use it to set rules, update software, monitor logs, and track network activity.
What are the key parts of a hardware firewall?
The main parts include processor, memory, network ports, firmware, and control panel. These parts work together to inspect and manage all incoming and outgoing network traffic.
Does a hardware firewall slow down the internet?
No, usually it doesn’t. In fact, hardware firewalls are designed to handle high-speed data traffic without affecting performance. They are faster than software firewalls in most cases.
